
Security is a primary concern for everyone in the digital age. We know strong passwords can mean the difference between a secure server and a compromised mess. But the strongest passwords have no value if a database is compromised and hackers get access to your credentials. So what more can a security-conscious person do? Two-factor authentication is the answer!
What is Two-Factor Authentication?
Two-factor authentication (2FA) is a security protocol that uses two different authentication methods at the same time, thereby strengthening security and preventing unwanted access to a system or account. Most 2FA systems use a combination of a password and some rotating alpha-numeric combinations to ensure that only the true owner of the credentials can access a system.
4 Types of Two-Factor Authentication

1. Biometric Systems
Many physical locations use a biometric two-factor authentication system to control access. In biometric authentication, the user first enters a password or passcode, then uses a physical confirmation of their identity. The physical component could be a thumbprint, a retinal scan, or even facial or voice recognition. The advantage of biometric authentication is that the user is always in possession of the secondary component because it is part of them.
Popular examples of devices that use biometric-based authentication include phones, tablets, and laptop computers.
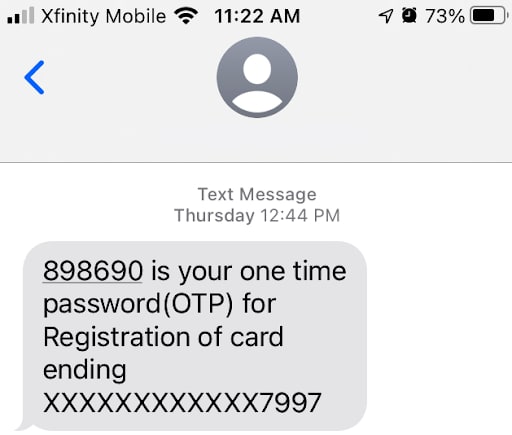
2. Text-Based Systems
Text-based two-factor authentication systems use SMS messaging to provide an additional layer of security against intrusion. Once the correct password is entered, the security system sends a text message to the user’s cell phone containing a one-time passcode. The passcode can then be entered into a security dialogue to allow access to a system. Similarly, some systems send an email to the user’s primary email address with a single-use passcode to provide the second step of the authentication process.
While text-based authentication is exponentially more secure than a password alone, both biometric authentication and third-party authentication are a more secure method, as SMS can be intercepted.
Popular examples of applications that use text-based authentication include Facebook and HubSpot.

3. Third-Party Application Systems
Third-party application authentication provides rolling security codes that can be used in combination with a strong password to protect your accounts and servers. Like the text-based authentication systems, the user enters their password, followed by the current code available in the application (typically, these codes rotate every 30 seconds to one minute).
Some apps even use push notifications to the app, allowing the user to confirm in the app that access has been requested and should be granted. Many users prefer this, as it is secure and provides quick access to the intended system without manually entering a one-time password.

4. Hardware-Based Systems
In hardware-based authentication systems, the user is given a physical device that provides a rotating series of passcodes to verify identification. Some of the most secure 2FA systems in use are hardware-based. These devices are similar to application-based systems but require the user to be in possession of the physical device to access the passcodes. ID badges are a less sophisticated version of hardware-based authentication, and are often used to provide access to a building or secure room.
The advantage of such devices is that only one person can be in control of the device and therefore have access to the system using a paired set of credentials. However, like any other object, hardware keys can be lost, making this authentication method prone to some risk of being locked out of your own systems.
Using Two-Factor Authentication
There are many possible applications for using two-factor authentication in your everyday workflow. Most email providers allow the use of 2FA to protect your important communications. Any credit card or banking accounts should be protected with two-factor authentication to ensure your money and digital identity remain protected from compromise and exploitation.
One of the most important uses of two-factor authentication is protecting access to your password manager. With every website and system requiring unique and strong passwords, most users implement a password manager to keep their various credentials securely stored in a single location. However, if all of your passwords are kept in a single database, a security breach could be catastrophic. Protecting your password management system with two-factor authentication is essential to keeping your credentials secure.
Setting Up Two-Factor Authentication
Passcode challenge systems are probably the easiest two-factor authentication systems to use. In these systems, you provide the security system with a reliable communication method when you set up your account (either an email address or phone number that is different from the login credentials for the system). Once you’ve entered your secure password, the system sends a message via your alternative communication method containing a one-time-use passcode. The passcode is generally a simple string of numbers, but it is only available for a short period of time, making compromise by a malicious user very difficult.
Application-based systems can be a little more complicated to set up but are often easier to use once configured correctly. For most applications, you are required to confirm a security token in the application when setting up access for a new account. You can generally use your phone and application to scan a QR code or follow a secure link to tie your device to the 2FA system and your account credentials. Once the application is configured for your account, you can view a time-sensitive passcode whenever you need access to your two-factor authentication. Because applications use a rotating code, you won’t be left waiting for an email or text message to arrive before you can authenticate your credentials. This instant access to the verification code makes third-party applications a valuable time-saver for users who need to access secure systems on a regular basis.
Two-Factor Authentication at Liquid Web
Two-factor authentication systems provide an extra layer of security for all your most important systems and services. You’ll be protected from compromised credentials because access requires both a strong password and another method of establishing your identity.
Don’t wait! Enable two-factor authentication for all your important systems today.
[ad_2]
Source link


![What is Two-Factor Authentication [4 Types and Setup]](https://dealzclick.com/wp-content/uploads/2022/02/Dyson-V11-Absolute-Pro-Vacuum-Cleaner-Review-Home-Cleaning-at.jpg)
![What is Two-Factor Authentication [4 Types and Setup]](https://dealzclick.com/wp-content/uploads/2022/02/Hot-New-Manifestation-offer-Pure-Natural-Manifestation.jpg)



