
[ad_1]
Out-of-date technologies are a security risk for software businesses. However, despite the problems with legacy systems, several companies continue using them.
More than 80 percent of the global organizations surveyed by VMware reported a security breach in 2020, and using outdated security technologies was one of the top three reasons for the compromise.
So, why are legacy systems still used?
Common reasons include high operational value, contractual obligations, and high modernization costs. No matter why your company uses outdated legacy systems, you can identify the warning signs of vulnerable software and implement changes to reduce risk.
Five Signs Your Legacy Software Needs More Security
The problems with legacy systems aren’t always obvious. You’ve probably experienced some of these without realizing your software is at risk.
Here are five warning signs that indicate your traditional software needs more security:
1. Relies on Unsupported Software
Third-party software reduces costs of development and ownership by eliminating worries about its maintenance or updates. However, when the software reaches End-of-Life or the vendor terminates support, this convenience becomes a compliance issue.
For example, CentOS 8 reached End-of-Life on Dec. 31, 2021, eight years ahead of its planned life cycle. This left CentOS 8 users with two options: Migrate to a new operating system or risk non-compliance due to a lack of software updates.
Health Insurance Portability and Accountability Act (HIPAA) and Payment Card Industry Data Security Standard (PCI-DSS) are a few frameworks that mandate using actively supported software.
Although the regulatory frameworks applicable to your software may vary, it’s likely non-compliant and liability if it uses unsupported technologies.
2. Slow and Crashes Frequently
Do you find yourself going “yeah, it always does that” or recommending workarounds each time your software slows down to a crawl or crashes out of the blue?
Limiting functionalities and implementing workarounds might get the job done for now. But they won’t tackle existing security vulnerabilities. Further, temporary fixes might lead to technical debt, complicating future upgrades and introducing unknown vulnerabilities.
Waiting a few minutes to generate a report is expected. But if you need workarounds to perform simple tasks, that’s a clear sign that your legacy software needs modernization.
3. Incompatible With the Latest Software
Whether it’s with an Enterprise Resource Planning (ERP), Point of Sale (POS), or Customer Relationship Management (CRM), your software will require integrations with the latest technologies.
But integrating legacy and modern software may require expensive workarounds. Something as simple as a lack of an API in the core can lead to poor performance, integrations, and security gaps.
Legacy software can’t keep up with changing encryption standards or support integrations needed to run businesses smoothly. Thus, your customers are more likely to move to your competitors than wait for you to address the problems with your legacy systems.
4. Contains Hard Dependencies

Keeping software up to date is a resource-intensive task. When you’re working on improving functionality, fixing bugs, and trying to keep up with the competition, it’s easy to lose track of dependencies.
It’s only when you upgrade a component such as MySQLi or PHP that you realize your codebase is full of dependencies and potentially unknown risks.
Software that relies on legacy technologies such as hardware, operating systems, and database structures can’t adopt new technologies or implement security measures according to current standards.
Legacy dependencies hurt organizational flexibility, business agility, employee productivity, and future opportunities. More importantly, they necessitate additional security.
5. Difficult To Maintain or Support
Legacy technologies often have complex code and functionality. It can be challenging to replace isolated components or find competent engineers to maintain the system.
As a result, operating costs can eat into your business capital and limit your ability to innovate or scale with demand. Moreover, when things go wrong, it results in expensive downtimes that hurt both your operating budget and business reputation.
Naturally, you need to invest in maintaining your software. But when maintenance costs exceed your research and development expenses, it’s a sign that your traditional software needs more security.
Four Ways To Overcome the Problems With Legacy Systems
Once you’ve identified the problems with legacy systems, it’s time to strategize ways to secure your software. You can approach legacy system modernization to improve security in several ways.
Here’s a quick overview of the top four ways to fix the problems with legacy systems:
1. Encapsulate
The easiest way to protect your legacy system is by limiting network access to its data and functions using a firewall. After air-gapping the software, you can expose its functions as services via API to continue using legacy technologies with high operational value.
This strategy lets you tackle the performance, compliance, and IT network infrastructure security issues of on-premises legacy software. However, air-gapping is a temporary fix. Encapsulating legacy technologies doesn’t address issues with maintenance or upgrades.
2. Rewrite
Rewriting the software to fix legacy dependencies might sound like the most logical software modernization strategy for your business. Rewriting software, however, can quickly become an execution nightmare as you dig into old code to decipher forgotten edge use cases.
A complete rewrite is your best option if:
- The software is mission-critical, and its core framework is deprecated.
- You’re having a tough time finding competent staff to maintain the software.
- The costs of maintaining the software exceed that of a rewrite.
Although rewriting lets you reconsider functionality and implement future-proof measures, it’s an expensive endeavor that can drain your company resources instead of using those resources for adding features, product offerings, or marketing your business.
3. Rehost
Rehosting your legacy software is one of the fastest ways to secure it and offers the lowest upfront cost and risk. This is because cloud solutions offer greater flexibility than on-site hardware solutions.
Moreover, it gives you more options to choose from based on your use case. You can either migrate your software to a public or private cloud solution.
Relocating to the public cloud offers lower costs and near-unlimited scalability. However, you may need to refactor your code to work on the public cloud infrastructure after data migration.
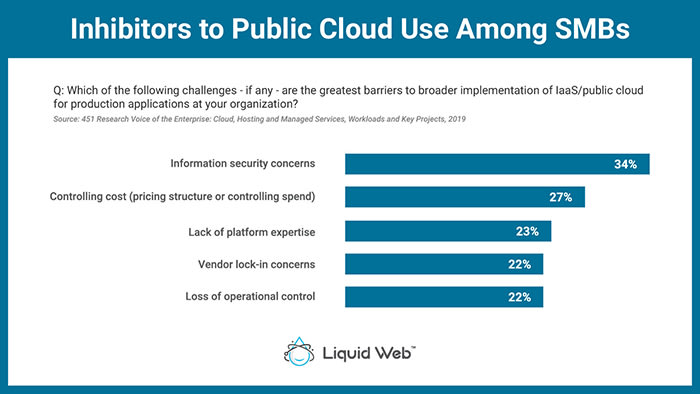
A survey by 451 Research found that controlling costs on the public cloud was one of the biggest challenges to adopting public cloud for small and midsize businesses. In contrast, managed private cloud offers a predictable yet cost-effective way to overcome the problems with legacy systems.
Migrating to a private cloud lets you leverage the flexibility and scalability of the cloud without worrying about infrastructure security. You can continue using your legacy software system in a secure, virtualized environment.
All you need to do is migrate your software to a hosted private cloud. Your hosting provider will handle the security and maintenance for you post migration.
4. Refactor
Refactoring your legacy software systems to work with the latest technologies is a low-risk option that solves compatibility and security issues. As you refactor, you can replace parts of your software, upgrade capabilities, and even reconsider your IT architecture.
The downside of refactoring is that it’s extremely slow, needs a lot of skill, and can often lead to more complexities in the long run. Make sure you properly estimate refactoring costs and plan them thoroughly before you opt for this approach.
Final Thoughts: Warning Signs Your Traditional Software Needs Additional Security
Navigating security problems with legacy systems is a never-ending challenge. However, the signs of vulnerable software systems are easy to spot. If your software shows any of the five warning signals we’ve listed above, it’s a clear sign that it needs more security.
Securing a legacy system is a complex task, and there’s no one right way to do it. Legacy system modernization strategies vary for each business. Make sure you weigh the pros and cons of each approach and choose the best one for your systems.
[ad_2]
Source link







