
It is hard to imagine running many businesses these days without information technology playing a pivotal role in your operations. Even the simplest of companies are somehow tethered to the Internet or have a measure of reliance on some simple IT infrastructure. So, what do you do when that little bit of IT infrastructure that your business relies on suddenly falls victim to those malicious hackers? With the increasing rate of cyberattacks, it’s just a matter of time before you encounter some hacking attempt, which is why your organization requires a cyber incident response plan.
Let’s explore what an incident response plan is, why it’s crucial to have one for every business, the most important parts to include in your plan, and the steps to create your first plan today.
What is an Incident Response Plan?
An incident response (IR) plan is a documented set of tools and instructions put together to help your team of information technology professionals identify, address, and recover from cybersecurity threats. A well-designed IR plan will help your IT staff quickly identify security threats and efficiently respond to them.
With an appropriate IR plan, if a security breach occurs, you have the right people, processes, and technologies to effectively take care of the breach and minimize the damage that it could cause.

Why is Having an Incident Response Plan Important?
The most obvious reason for having an incident response plan is to prevent a business loss due to cyberattacks. It seems like security analysts discover a new software vulnerability every other day, or there’s a report about a security breach exposing personal information for millions of people.
According to some analysts, data breaches exposed over 36 billion records in the first half of 2020.”
Falling victim to even one of these cyberattacks can cause irreparable damage and cripple your operations. An IR plan plays a vital role in helping you:
- Identify threats before they can cause damage. Rather than waiting to become another statistic in the ever-growing number of cyberattack victims, a cyber incident response plan will help your team respond to the seemingly inevitable attention from malicious actors.
- Prevent data loss if you experience a data breach from an intrusion attempt that was successful despite your best efforts. That’s because your planning activities will include data recovery procedures that will ensure your data is secure.
- Learn from previous security incidents and improve your organization’s capacity to handle future intrusion attempts.
- Save money that you would have spent on recovering from the damage that an unexpected security incident would have caused if your organization didn’t have an IR plan in place with procedures to mitigate the damage.
- Enhance your security posture. Sometimes, this is enough to serve as a deterrent to those looking to exploit weaknesses in your systems. It also means that when incidents occur, your team will spend less time figuring out what’s happening and instead focus on a swift resolution.
- Maintain business continuity and resilience because your organization must continue to deliver value to its customers no matter what happens. A proper incident response plan plays a vital role in your organization’s business continuity planning.
- Ensure compliance with an increasing number of new laws and industry regulations demanding that companies have procedures for detecting, responding to, and reporting security incidents.

The Six Stages of Every Incident Response Plan
Hopefully, you’re following along and are convinced about the importance of a cyber incident response plan to your organization’s sustainability. In that case, you should also know that every proper IR plan should have the following phases if it’s going to serve its purpose effectively:
1. Preparation
The preparation stage of your IR strategy involves laying the groundwork to ensure your business will be ready to face a security breach. Activities in this stage include carrying out a risk assessment and using the results to develop the security policies that will protect your critical infrastructure from identified cybersecurity threats. In addition to this, training your security teams on their roles and responsibilities, along with regular incident response drills, will help evaluate your readiness and identify and fix gaps.
2. Identification
Laying the proper foundation in the preparation stage will leave your team adequately prepared for what comes in this next phase. While monitoring your organization’s operations, the IR Team should be quick to identify unusual activity and determine if a security breach causes these activities.
If a security breach has occurred, the immediate focus should be on gathering and documenting as much evidence as possible about the incident. This documentation will inform your decisions in the next stage of your response plan.
3. Containment
You’ve correctly identified a breach in your systems and understand the attack’s scale and what parts of your infrastructure are affected. The next step is containment, and the evidence you’ve collected about the attack will determine your containment protocols.
Your goal here is to prevent the attackers from infiltrating more of your infrastructure. Short-term containment strategies may involve isolating the affected systems or spinning up backup servers, and diverting traffic to them so that business functions tied to those systems remain operational. Long-term containment protocols involve forensic operations on the affected systems and applying security patches to restore functionality.
4. Eradication
Once you’ve successfully contained the incident and prevented it from spreading, the eradication phase begins. Depending on the type of breach, eradication activities can include improving authentication systems, removing malware, disabling compromised accounts, and patching software vulnerabilities. The result of this should be the total elimination of threats and vulnerabilities from your operating environment.
5. Recovery
The recovery phase involves restoring all affected systems to standard operating capacity and ensuring there are no repeat incidents. Systems are recovered from backups and closely monitored for a fixed time to ensure optimal performance.
6. Lessons Learned
The last stage of your incident response plan occurs when you have thoroughly neutralized the threat and all systems have resumed normal operations. In this phase, your incident response team members will meet to document and analyze everything about the security breach. Asking questions during this phase will help identify areas that need strengthening. Try asking questions such as:
- How did the breach occur?
- How quickly did we respond?
- What needs improvement?
These types of questions will help solidify and close any missed loopholes or vulnerabilities.
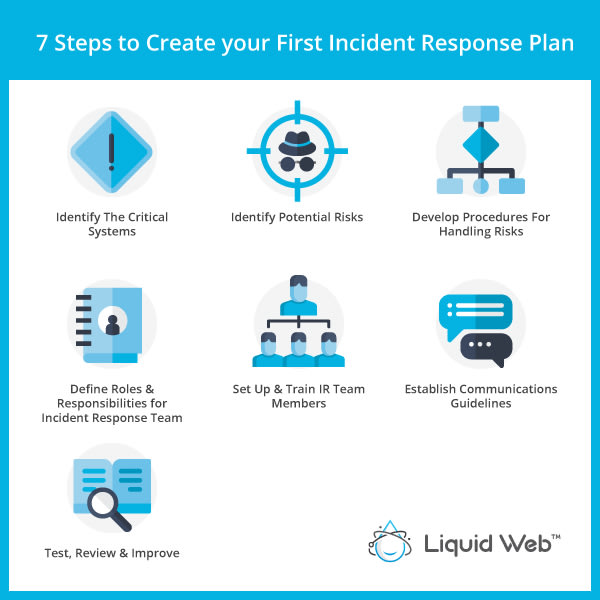
Seven Steps to Create your First Incident Response Plan
You don’t have to start from scratch when creating your incident response plan since there are several templates to get you started. The National Institute of Standards and Technology’s Computer Security Incident Handling Guide is a great starting point.
However, if you want an incident response plan that suits your organization’s unique setup, some activities must occur. These activities aim to provide you with a better understanding of your organization’s security posture, which will help you create a more effective IR plan.
1. Identify the Critical Systems
To adequately protect your infrastructure against cybersecurity incidents, you must first identify those systems that are most critical to your business operations. Ask yourself what pieces of equipment or data would cause your business the most harm if hackers attacked. Once you’ve identified them, prioritize them according to importance and risk exposure.
2. Identify Potential Risks
If you’ve picked out the assets critical to your operations, you also need to identify the possible threats to these systems. Researching the ways malicious actors exploit similar systems and understanding your industry are the key to clearly identifying the potential risks you face, your level of exposure, and the likelihood of occurrence.
3. Develop Procedures for Handling Risks
For each risk identified, you must develop procedures for dealing with it. Sometimes, these may be immediate steps to improve a particular system’s security, like patching a known software flaw or installing physical measures like security doors. Other times, your procedures will have no immediate steps to be taken but rather guidelines on how you should respond if a threat event occurs. These guidelines could include identifying and restricting an intrusion attempt or how to recover from a ransomware attack.
4. Define Roles and Responsibilities for Incident Response Team
Your incident response team will consist of individuals who will bear responsibility for your IR plan’s activities and ensure that security incidents do not adversely impact your organization’s essential functions. An IR team’s size will vary depending on the size of an organization and the infrastructure scale, so it’s important to note that one person may play multiple roles in a team for a smaller organization.
5. Set Up and Train IR Team Members
Speaking of effective job handling, informing each IR team member of their positions’ requirements is necessary for their effectiveness. The team members do not all have to be cybersecurity experts because there are a few roles that require expertise in other fields, such as the legal representative or the communications leader. The important thing is that the team members receive security awareness training to handle their jobs effectively.
6. Establish Communications Guidelines
Communications guidelines are essential when it comes to incident response and management. The speed and effectiveness of your communications have a direct impact on your team’s responsiveness to threats. Therefore, establishing protocols for relaying information between team members, other staff, and external stakeholders like security agencies, service providers, and clients is essential to your plan’s success.
7. Test, Review, and Improve
The constantly evolving threat landscape means you need to regularly test your incident response plan and refine it based on your test results. Tests could be in the form of planned or unplanned security drills, simulations, and tabletop exercises designed to familiarize your employees with the IR plan’s contents. In addition to this, your test results will identify gaps that your IR team will address.
Security Beyond Incident Response With a Security-Focused Cloud Provider
Without a doubt, reducing vulnerability to cybersecurity threats should be a priority for any modern business. Putting the proper systems in place to combat these threats can substantially burden the resources available to your organization. However, you can ease that burden by moving to a cloud-based setup such as VMware Private Cloud. That’s because while they can improve efficiency and reduce costs, the right cloud service provider can also strengthen your entire infrastructure’s security with knowledgeable cloud security expertise and valuable security add-ons.
[ad_2]
Source link


![Incident Response Plan [7 Steps to Create One Now]](https://dealzclick.com/wp-content/uploads/2022/02/Acer-Predator-Helios-500-PH517-52-With-11th-Gen-Intel-Core.jpg)
![Incident Response Plan [7 Steps to Create One Now]](https://dealzclick.com/wp-content/uploads/2022/02/1643903563_Unauthorized-Affiliate-error-page.jpg)



