
Data privacy for remote workers is essential – it always has been – but now, more than ever, it is dominating the cybersecurity strategies of all businesses with a staggering 4.7 million people in the U.S. now working remotely.
But, with increasing levels of cybercrime and remote workers being targeted, it begs the question: How do we protect the privacy of remote workers and company data?
Last year, 4.1 billion data records were exposed due to data breaches, illustrating just how important it is for companies and remote workers to ensure that their data is kept safe and out of the hands of hackers.
So, with that in mind, let’s take a look at the five tips you should follow to ensure the privacy of your data.
1. Store Your Passwords in an Encrypted Vault
Every online account is protected by a password, but just how safe are they? The truth is that most of the passwords we use are not all secure. The reason why: entropy.
Entropy is the measurement of the randomness or diversity of a data-generating function.
Passwords with high entropy are completely random and have no meaningful patterns, making them almost impossible to crack.
Unfortunately, the average person can’t memorize complex random passwords, meaning human-generated ones tend to only be about 40 bits of entropy.
To put this into perspective, a password with 128 bits of entropy is virtually unbreakable; therefore, 40 bits give hackers a much higher possibility to predict the value.
With the average person having 70-80 passwords, the sheer volume that we have to remember makes us prone to unsafe password practices such as recycling old passwords or using the same ones for multiple accounts.
Hackers are well aware of these cyber hygiene pitfalls, and exploit them regularly for financial gain. No country or business is immune, and exposure to cybercrime is rife.
Poor password practices compound remote working risks, as employees often opt for convenience over security, saving sensitive login credentials using unsecured methods including spreadsheets, notes of paper, and sharing them over email.
The most effective way to protect credentials from malicious hackers is to store them in an encrypted password vault, otherwise known as a password manager.

Password managers facilitate security and convenience by enabling businesses to add, edit, and store an unlimited number of passwords in a securely encrypted vault.
Therefore, your remote team no longer needs to remember long complex passwords. Instead, they can rely on the software to automatically fill the login credentials whenever they need them.
The zero-knowledge security models employed by password managers also lends itself to full data privacy where the software never sees or stores your unencrypted passwords on their servers.
If a hacker managed to hack the servers where your data is stored, they would only see streams of encrypted code that is meaningless and not of any value.
Ultimately, password managers enable remote workers to save unique passwords with high levels of entropy for each account in securely encrypted vaults to strengthen the security of business accounts.
They can also play a key role in ensuring complete data privacy is via single sign-on solutions that make business-critical accounts accessible in one convenient portal.
Remote workers simply need to login to the vault, click on the account they need access to, and they will be logged in automatically without ever seeing the login credentials.
2. Shield Your Data From Prying Eyes

One of the main challenges that IT staff face with remote workers is the conundrum of providing them with a safe and secure way of accessing company resources while maintaining security and optimal network speeds.
This is where a VPN, or virtual private network, comes into play.
VPNs form the basic backbone of remote working security and provide workers with a secure method to connect to company resources, such as shared files. More than 400 million businesses and consumers are already making use of VPN connections, and this number continues to grow as more people start working from home.
Working remotely without using a VPN poses a serious security risk, since it makes it much easier for hackers to intercept confidential company data as it travels between your remote location and the office.
A VPN can be compared to a private tunnel that links your remote location directly with your office, and since the data that travels in this tunnel is shielded from view, it is much more difficult for hackers to intercept and steal sensitive data.
They can be used to connect to most remote resources, including mail servers, CRM programs and software, and even accounting systems.
It is especially important to use a VPN in cases where remote employees use their computers for both their personal and professional computing needs.
Employees can often unknowingly download emails or other files that have been infected with malware, and in doing so, expose confidential company data.
3. Secure All Your Devices, Not Just Work Ones
Endpoint security, in its simplest form, refers to the practice of securing the individual devices that connect to a network, such as laptops and mobile phones.
While securing you can enhance the protection of your cloud assets through security and compliance add-ons, endpoint security includes software such as antivirus, antimalware, and firewall programs, and it forms an essential part of any remote worker’s security arsenal.
However, it is important to remember that endpoint security does not just refer to the likes of antivirus software, but it also includes the way that we interact with our devices.
In order to reduce security vulnerabilities and the risk posed by hackers, remote workers should adopt safe computing practices, such as avoiding potentially malicious websites and not opening emails that may contain dodgy attachments.
Whilst working from home can often make us less vigilant to the threats that we face, it’s worth noting that endpoint devices are the second most targeted type of asset in data breaches, following servers.

Remote workers that choose to use their own devices for both work and personal use can create an avenue for hackers to worm their way into company systems if they are not properly protected.
It is therefore essential that remote workers notify IT teams of the devices they use to access business systems.
Because endpoint security solutions are often cloud-based, they can be easily distributed across devices remotely.
Alternatively, if you are not able to install the appropriate security software, it is best to only use the devices granted to you by your business, since these will have already been factored into your company’s IT security network and infrastructure.
The global endpoint security market is predicted to be worth $10.02 billion by the end of 2026, up from 5.30 billion USD in 2018.
This is an indicator of just how important it is for both corporations and end-users to invest in endpoint security if they have not already done so.
4. Use Encrypted Communication Platforms
Communication is key in every business, and it is even more important in remote working environments.
We often hear of hacked email accounts and the exposure of confidential business communications that have serious implications for data privacy.
But as businesses increasingly opt for chat-based and online meeting platforms, it becomes ever-more important to secure these newly adopted communication channels.
For this reason, consider using a secure and customizable CPaaS platform to secure your data and get your messages across.
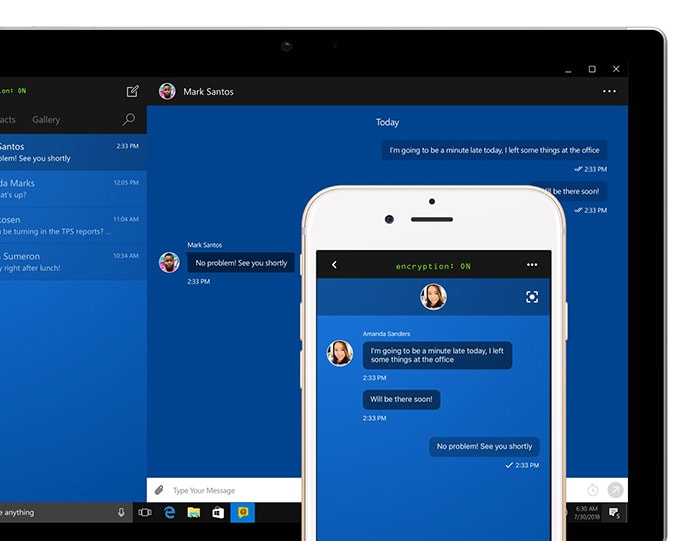
Not only do chat applications facilitate higher levels of productivity, thanks to a more seamless communication method than email, but some also offer data privacy.
Secure chat applications, like Keeper Chat, encrypt messages before they are sent to the intended receiver. Should the message be intercepted by a hacker, they cannot be read, and your information stays private.
The benefit of these applications is that they are web-based and, therefore, offer cross-platform and device compatibility, making them ideal for remote working where they can be accessed anywhere, anytime.
5. Protect Yourself Beyond Software
Aside from using security software, there are a few other things that you can do to keep your data safe.

Log Out Whenever You Leave Your Workspace
It is important to remember that public spaces are not as safe as the office spaces that we are accustomed to working in, and you should never leave your computer unlocked when it is not in your possession. An unlocked computer that is logged into secure company networks is a prime target for hackers, so make sure to log out before you leave.
Do Not Connect to Public Wi-Fi Hotspots
Public Wi-Fi often has little to no security, and you should avoid connecting your computer or smartphone to a public network whenever possible to protect yourself from malicious actors. A good alternative to a public hotspot may be bringing your own mobile data connection with you when you have to work outside of your usual workspace. Or, if you have no choice but to connect to a hotspot, use a VPN.
Physically Secure Your Devices
When you are working in a public space, you should consider using physical security devices such as a kensington lock to secure your laptop.
Ensure Your Business Documents Are Secure
With more businesses signing documents online and keeping important files in the cloud, you need to ensure their security. Use encrypted e-signature software and strong password protection for your business documents.
Adopt Remote Work Security Best Practices Today
Working remotely has become the new reality for many of us and it is somewhat unfamiliar territory.
By adopting these simple security practices, using the appropriate software to protect your data from prying eyes, and most importantly, maintaining good cyber hygiene, you will drastically improve your data privacy.
Struggling to Secure Your Entire Infrastructure? Download our Security Infrastructure Checklist.
[ad_2]
Source link


![Remote Work Security [5 Data Privacy Tips]](https://dealzclick.com/wp-content/uploads/2022/02/Cheat-Codes-of-the-Universe.jpg)



