
What is Phishing?
Phishing is the exploitation of any weaknesses, whether technologically or in humans, to gather personal and/or sensitive information from an individual or organization for fraudulent activities. The attacks are performed by impersonating a trusted entity, usually via email, telephone (vishing), or private messages (smishing).
Phishing will be looking to steal the following types of sensitive information:
- Passwords
- Usernames
- Social security numbers
- Access codes
- Banking details
- Medical records
Once the attackers obtain this information, it is then used to threaten the affected parties for compensation, steal vital information, or access important accounts. This can end in financial loss, impacted reputation, and compromised sensitive data for the targeted organization.
The origin of this malicious practice can be traced back to the mid 90s, around the year 1995. The first wave of phishers achieved a significant success rate because these types of scams were unknown at the time.
America Online (AOL) was one of the major Internet providers and had moderated success with other Internet services. A group of hackers called the “warez community” started stealing other users’ credentials and used them to generate fake credit cards to open fake AOL accounts to spam even more users. AOL eventually put an end to these incidents with strong security updates, but the attacks evolved as usual. The new method was to impersonate AOL employees and request users to “verify” their accounts, including, of course, billing information updates. Since phishing practices were only known to enthusiasts and professionals, most users fell victim to scams.
Sadly, and even though the tactics and trends have become more refined, the essence of phishing remains the same, simply because they target our weaknesses as human beings (curiosity, unawareness, ignorance, etc.).
The Anatomy of Phishing
There is a wide variety of ways to execute phishing; however, we can separate each interaction’s most common and fundamental elements. Our focus is on email phishing, but this can also apply to SMS phishing (smishing) or voice phishing (vishing).
Unusual Offers or Notifications
Offers coming from companies we have never heard of, never had an affiliation with, or that we are unsure how they got our contact information could be phishing. These offers are usually extremely noticeable and impressive (most of the time, too good to be true), which is a common practice among bulk phishing.
Top Priority
These emails are embedded with a sense of immediate action and urgency, with the risk of facing such consequences as permanent deactivation of accounts, cancellation of memberships, or losing a once in a lifetime opportunity, among others.
The Sender and Receiver
Unless the trusted entity was compromised, the sender’s name will never match the original name in the email. Attackers are always looking to deceive victims by using domains that are similar in nature. For instance, an attacker may use paypa1.com instead of paypal.com, or Aṁazon.com instead of Amazon.com. This is an immediate red flag that the email is not legitimate. Most of the time, however, they use any domain name available, and instead modify the “From” to simulate a legit sender.
The receiver can also be vital to review. If the email was sent to several unrelated users (bulk phishing), or if your email is not explicitly in the list of receivers (it was sent to a mail list instead), that can be a reason to distrust the email and sender.
Attachments/Hyperlinks
The true motive of these attacks is to compel the user into downloading a malicious file (malware), accessing a compromised website, or revealing information. They will often include the “solution” to your urgent matter within the email in the form of a file, verification link, or form to fill out.
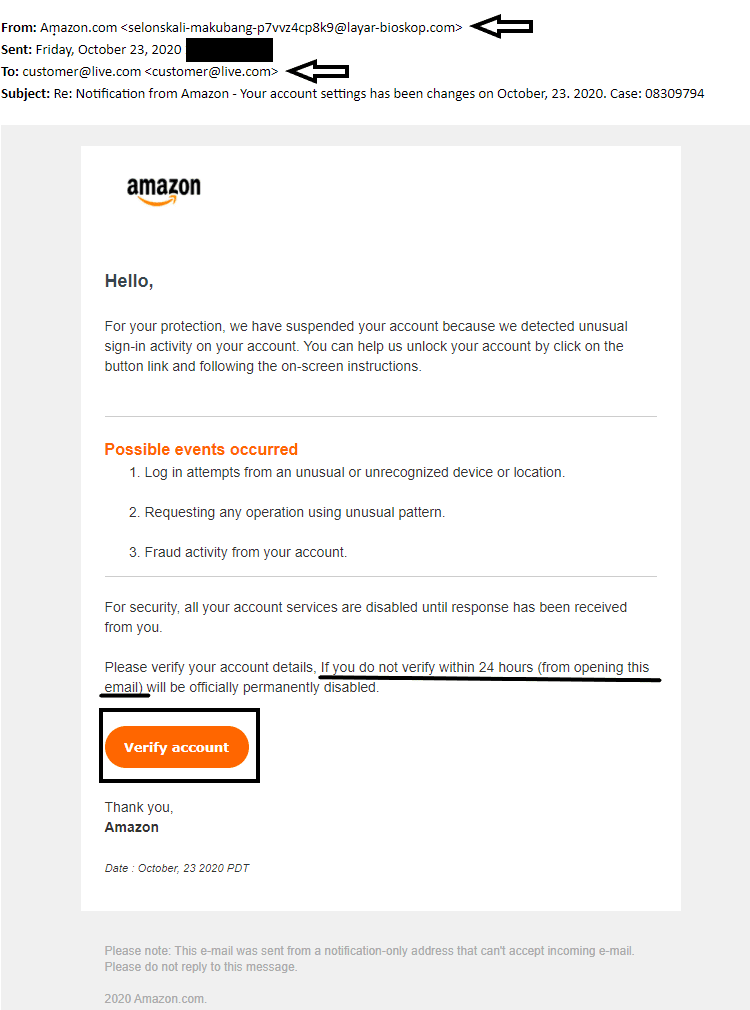
From the image above, we can conclude that this is a phishing scam.
First, look closely at the “From” address: it has been camouflaged with foreign characters to appear legitimate, but the real address sending the email is <selonskali-makubang-p7vvz4cp8k9@layar-bioskop.com>.
We can also notice that the “To” address is not our specific address, but customer@live.com. The redaction of these emails usually comes with a few grammatical errors, but the main points here are the sense of “urgency” and the immediate solution. They claim that actions will be taken if an issue is not addressed right away and present a link to “resolve” the situation, which redirects you to a clone of the official site, modified to take your credentials and sent them to the attacker.
In this scenario, the absolute best action is to not respond to the email, not click any links in the email, and not download any email attachments. Instead, go to the actual site (in this case, Amazon’s site) and verify your account status.
Phishing Methods
There are several approaches and trends in the phishing world. Even though most of them include the common elements described in the previous section (malicious links and attachments), that doesn’t stop these criminals’ creativity.
The five most common phishing methods are the following:
Threat Phishing
Threat phishing is a common operation method. The aggressors claim to have vital information about an individual or organization, and they demand an untraceable transaction (usually using cryptocurrency) to delete the information or unlock the system. The difference between this and a ransomware attack is that the criminal is just bluffing. Most of the time, the email itself contains attachments or links with real ransomware that can compromise the organization. Lately, even organizations we considered off-limits, such as hospitals, are being targeted.
Account Verification
In this scam, you are asked to update or verify your account information, revealing usernames and passwords; emails, account numbers, and phone numbers; and other relevant information to the attacker. This is the oldest method of phishing.
Payment Failed
In this method of attack, you are required to update your banking details (and even social security numbers) because your recent “payment” failed and your order can’t be delivered. This tactic is also used to refer to delivery failures. This is a frequent mechanism used for identity theft.
Invoice/Taxes
This scheme consists of an urgent letter from a tax administration agency stating that you have a pending balance. To avoid legal action, you’ll need to issue payment to a specific account (which is not a government account). This is not limited to tax organizations. The email, text, or call may also imply that you solicited an illegal service and need to pay a fine to avoid penalties or that you have a pending invoice from an unpaid service acquired years ago.
Social Media Phishing
Social media phishing is becoming one of the most popular entry-points for phishers. Given the massive user base of these platforms, it’s easy to scale the scam to reach a vast number of people. These scams may include romantic entanglements to induce later extortion, clicking on a link advertising free trials or amazing offers, suggestions to make a phone call for a premium service (which turns out to be a phone number with a premium rate that skyrockets your bill), or scammers impersonating trusted individuals to ask for money.

Types of Phishing
There are three main types of phishing scams:
Bulk Phishing
Bulk phishing is the most general form of phishing and relies on the attacker sending the same scam message to the largest possible number of targets, regardless of their particularities. The low rate of individual success is often compensated by the huge amount of emails/messages sent.
Spear Phishing
This is one of the most dangerous modes of phishing because it can translate into substantial financial and data loss for organizations. It involves the preparation work of exploration and investigation of the target before perpetuating the cyber attack. Spear phishing is usually the result of a combined effort, for instance, social media phishing and stalking, among other information sources. The target falling into the scam is just the first step, which involves getting privileged credentials or automatically installing malware onto the target’s computer. The malicious software can later spread across the entire network, or keep a low profile to gather information for an undetermined period, or both. This can create unimaginable consequences to any business, from extortion to permanent reputation damage, and hence the importance of taking security as a serious matter.
Whaling
Whaling is a sophisticated phishing attack with a focus on the high-level executives of a targeted company. The primary reason this form of phishing is chosen is that these executives usually don’t have strict network restrictions, so it’s often easier for scammers to seep malicious software. This type of shakedown can also carry all the consequences of spear phishing emails.
SSL Certificates and Phishing
In the past, one way users determined if a site was trustworthy was by looking for the browser’s lock symbol, indicating the site was protected by an SSL certificate (HTTPS). In order to be issued an SSL, you needed to verify your identity, and most scammers could not do so.
The protocol has changed.
With automation in the verification process, cybersecurity has increased as most sites now encrypt our information; however, this has also created a window for bad actors to obtain them easily. More than half of phishing sites now use the HTTPS protocol. Of course, these sites are quickly targeted, and most browsers will give alerts to the users, but a few have most likely already fallen prey to the sham by that time.
How Do You Protect Your Business Against Phishing?
Phishing is still a problem because it uses social engineering to specifically target our flaws as humans, which explains why the model has not changed a lot in more than two decades.
Social engineering is not limited to the digital world and has been an art since the beginning of humanity. Social engineering is the ability to use any means necessary to exploit a target into giving valuable information, usually involving knowing the target’s patterns, tendencies, and emotional frame. We have a natural inclination to trust, which is widely used by criminals, including phishers.
For this reason, the best way to protect your business against phishing is by providing proper training for your employees. Security awareness training must be a regular practice, along with email security guides. This alone can dramatically decrease the entry vectors for phishing incidents because it goes to the root cause of the matter. Of course, we can set up technology solutions to further improve phishing detection.
Anti-Phishing Software
Anti-phishing/anti-spam software is an essential addition nowadays to any business network. It will identify and discard the most common ways of phishing/spam. Of course, even with the inclusion of artificial intelligence and neural networks to these solutions, the most sophisticated attempts might be able to bypass the filter, which is when employee awareness and training comes to play.
Links and Attachments Limiters
Another great solution is incorporating tools to redact all links automatically in email communication within the network, thus diminishing the danger of the few emails that bypass the anti-phishing software.
The benefits of implementing these measures are crystal clear: making your network less susceptible to attacks that can lead to, more often than not, economic damages, possible legal action for privileged information diffusion, broken reputation, and irreparable injuries in infrastructure.
Liquid Web Can Help!
If you need additional and more specific tips about cybersecurity, check out our video series, or take a look at our security and compliance services. Need help? You can open a live chat with us or give us a call at 1-800-580-4985. Our technical support staff is available 24/7/365 to assist if you need additional information related to phishing. Support is also available via our ticketing systems by emailing us at support@liquidweb.com.
[ad_2]
Source link


![What is Phishing [How it Works & Best Ways to Protect From]](https://dealzclick.com/wp-content/uploads/2022/02/Realme-Buds-2-Neo-Earphones-Launched-in-India-Alongside-Beard.jpg)
![What is Phishing [How it Works & Best Ways to Protect From]](https://dealzclick.com/wp-content/uploads/2022/02/Sacred-Geometry-Manifestation-Pendant.jpg)



